Wfuzz is a tool for bruteforcing Web Applications, it can be used for
finding resources not linked (directories, servlets, scripts, etc),
bruteforcing GET and POST parameters for different kinds of injections
(SQL, XSS, LDAP, etc.), bruteforcing form parameters (user/password),
fuzzing, and more.
Wfuzz - The web bruteforcer
-
Wfuzz is a tool designed for bruteforcing Web Applications, it can be
used for finding
resources not linked (directories, servlets, scripts, etc), bruteforce
GET and POST parameters for checking different kind of injections (SQL,
XSS, LDAP,etc), bruteforce Forms parameters (User/Password),
Fuzzing,etc.
It's very flexible, here are some functionalities:
- -Multiple injection points (no limits)
- -Post, headers and authentication data bruteforcing
- -Output to HTML
- -Colored output
- -Hide results by return code, word numbers, line numbers, etc.
- -Encodings: sha1,md5,urlencode,uri_hex,utf8,double_urlencode,binary_ascii, and many more.
- -Cookies fuzzing
- -Multithreading
- -Proxy and SOCKS support
- -Multiple FUZZ capability with multiple dictionaries
- -Authentication support (Ntlm, Digest,Basic)
- -Time delays between requests
- -Verbose output
- -Flexible payloads (permutation,range,files,usernames,etc)
- -Recursion (When doing directory bruteforce)
- -Payload combinations with iterators
- -Baseline request (to filter results against)
- -Brute force HTTP methods
- -Multiple proxy support (each request through a different proxy)
- -HEAD scan (faster for resource discovery)
- -Dictionaries tailored for known applications (Weblogic, Iplanet,
Tomcat, Domino, Oracle 9i, Vignette, Coldfusion and many more.
(Many dictionaries are from Darkraver's Dirb, www.open-labs.org)
It was created to facilitate the task in Web Applications assessments, it's a tool by pentesters for pentesters ;)
One of the strengths of wfuzz is the speed, just try it...
- How does it works?
-
UPDATE: go to the WIKI page in Google code for the latest documentation wiki
- Examples
-
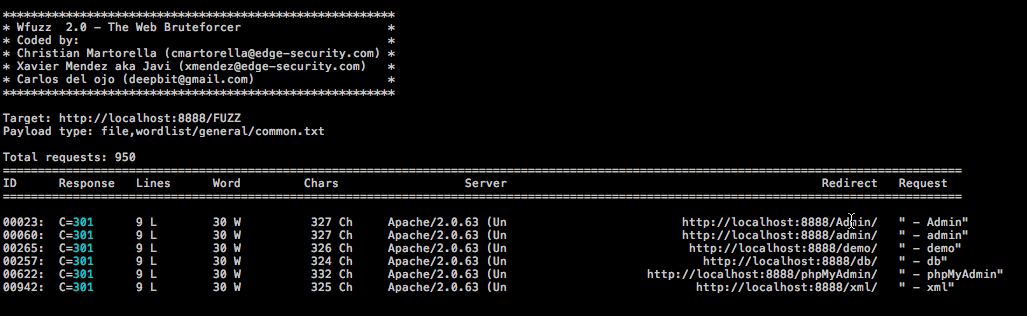
- wfuzz.py -c -z file -f wordlists/commons.txt --hc 404 --html http://www.mysite.com/FUZZ 2> results.html
- This will bruteforce the site http://www.mysyte.com/FUZZ in search of resources (directories, scripts,
files,etc), it will hide from the output the return code 404 (for easy reading the results), it will use the
dictionary commons.txt for the bruteforce, and also will output the results to the results.html
file (with a cool format to work).
wfuzz.py -c -z range -r 1-100 --hc 404 http://www.mysite.com/list.asp?id=FUZZ
- In this example instead of using a file as dictionary, it will use a range from 1-100, and will
bruteforce the parameter "id".
wfuzz.py -c -z file -f wordlists/commons.txt --hc 404 --html -d "id=1&catalogue=FUZZ"
http://www.mysite.com/check.asp 2 > results.html
- Here you can see the use of POST data, with the option "-d".
wfuzz.py -c -z file -f wordlists/commons.txt --hc 404 -R 1 http://www.mysite.com/FUZZ
- Example of path discovery, using a recursive level of 1 paths.
wfuzz.py -c -z file -f wordlists/Injection/SQL.txt -V allvars http://www.mysite.com/res.asp?id=1&name=cars&cat=2
- Example of Sql injection on every parameter of the request, you can fuzz every parameter with the option "-V allvars".
download coming soon.





 3:25 PM
3:25 PM
 Unknown
Unknown

 Posted in:
Posted in: 

.jpg)

0 comments:
Post a Comment