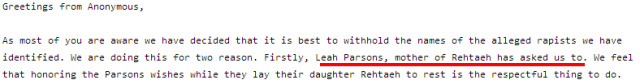LivingSocial, the daily deals site owned in part by Amazon, has suffered a massive cyber attack on its computer systems, which an email from CEO Tim O’Shaughnessy — just sent to employees and obtained by AllThingsD.com — said resulted in “unauthorized access to some customer data from our servers.”
The breach has impacted 50 million customers of the Washington, D.C.-based company, who will now be required to reset their passwords. All of LivingSocial’s countries across the world appear to have been affected, except in Thailand, Korea, Indonesia and the Philippines, as LivingSocial units Ticketmonster and Ensogo there were on separate systems.
One positive note in a not-so-positive situation: The email sent to employees and customers noted that neither customer credit card nor merchant financial information was accessed in the cyber attack.
This is the latest big data breach in the consumer Internet space, which has seen troublesome incursions into some high-profile companies recently, including Zappos, LinkedIn and Evernote.
When asked for comment on the email, a LivingSocial PR spokesman confirmed the attack and that 50 million customers were impacted.
The attack comes at a tough time for the company, since it has been trying to turn itself around after a downturn across the daily deals landspace. LivingSocial got a large cash infusion recently from investors to help staunch its losses. Amazon owns 29 percent of the company.
More to come, but here’s the email sent to employees, including one that will be sent to customers soon:
Re: Security Incident
LivingSocialites –
This e-mail is important, so please read it to the end.
We recently experienced a cyber-attack on our computer systems that resulted in unauthorized access to some customer data from our servers. We are actively working with law enforcement to investigate this issue.
The information accessed includes names, email addresses, date of birth for some users, and encrypted passwords — technically ‘hashed’ and ‘salted’ passwords. We never store passwords in plain text.
Two things you should know:
1. * The database that stores customer credit card information was not affected or accessed.
2. * The database that stores merchants’ financial and banking information was not affected or accessed.
The security of our customer and merchant information is our priority. We always strive to ensure the security of our customer information, and we are redoubling efforts to prevent any issues in the future.
To ensure our customers and merchants are fully informed and protected, we are notifying those who may have been impacted via email explaining what happened, expiring their passwords, and requesting that they create new passwords. A copy of the note is included below this email.
If you have any questions or concerns, please visit Pulse –https://pulse.livingsocial.com/intranet/Home/more_updates.html — for a list of frequently asked questions. If you have additional questions that aren’t answered in the FAQs, please submit them via email to XXX@livingsocial.com.
Because we anticipate a high call volume and may not be able to answer or return all calls in a responsible fashion, we are likely to temporarily suspend consumer phone-based servicing. We will be devoting all available resources to our web-based servicing.
I apologize for the formality of this note, which the circumstances demand. We need to do the right thing for our customers who place their trust in us, and that is why we’re taking the steps described and going above and beyond what’s required. We’ll all need to work incredibly hard over the coming days and weeks to validate that faith and trust.
– Tim
Subject: An important update on your LivingSocial.com account
LivingSocial recently experienced a cyber-attack on our computer systems that resulted in unauthorized access to some customer data from our servers. We are actively working with law enforcement to investigate this issue.
The information accessed includes names, email addresses, date of birth for some users, and encrypted passwords — technically ‘hashed’ and ‘salted’ passwords. We never store passwords in plain text.
The database that stores customer credit card information was not affected or accessed.
Although your LivingSocial password would be difficult to decode, we want to take every precaution to ensure that your account is secure, so we are expiring your old password and requesting that you create a new one.
For your security, please create a new password for your < > account by following the instructions below.
1. Visit LivingSocial.com
2. Click on the “Create a New Password” button (top right corner of the homepage)
3. Follow the steps to finish
We also encourage you, for your own personal data security, to consider changing password(s) on any other sites on which you use the same or similar password(s).
The security of your information is our priority. We always strive to ensure the security of our customer information, and we are redoubling efforts to prevent any issues in the future.
Please note that LivingSocial will never ask you directly for personal or account information in an email. We will always direct you to the LivingSocial website — and require you to login — before making any changes to your account. Please disregard any emails claiming to be from LivingSocial that request such information or direct you to a different website that asks for such information.
If you have additional questions about this process, the “Create a New Password” button on LivingSocial.com will direct you to a page that has instructions on creating a new password and answers to frequently asked questions.
We are sorry this incident occurred, and we look forward to continuing to introduce you to new and exciting things to do in your community.
Tim O’Shaughnessy
CEO, LivingSocial







 4:05 AM
4:05 AM
 Unknown
Unknown




















 If
there is one thing that is consistent about Anonymous barging into high
profile cases, it that one way or another they manage to screw up the
lives of innocent people with their actions.
If
there is one thing that is consistent about Anonymous barging into high
profile cases, it that one way or another they manage to screw up the
lives of innocent people with their actions. Somehow, Anonymous got involved and started
Somehow, Anonymous got involved and started